Communicate Complex Cybersecurity Needs to Municipalities, Enterprises and SMBs

(This image was generated with Canva’s AI tool)
When organizations get cybersecurity platforms and consultations, they often don’t just click a button. They want to first verify they’re getting…
=> The most trusted solution
=> The kind that deeply understands their challenges and aspirations
=> And is sensitive to the needs of their entire buying committee.
The best cybersecurity writers will help you feel the same about the content you produce.
=> Yes, your writer needs to understand innovative technology, but…
=> Also get the complexities that go on behind the scenes.
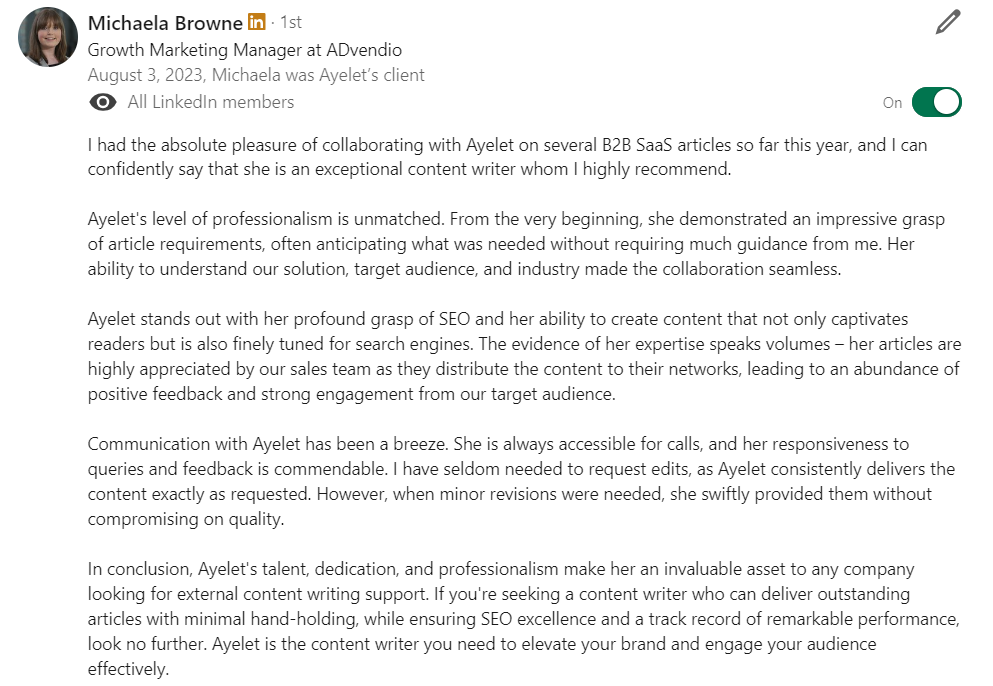
My expertise in writing for business audiences (across the c-suite and all levels of management) adds an essential layer to my work as a freelance cybersecurity writer.

– Revital Libfrand, CMO at odix, a leading provider of advanced content disarm and reconstruct (CDR) solutions for eToro, the Ministry of Health, Tel Aviv Municipality and the European Investment Bank, among others.
The Freelance Cybersecurity Writer that Will Help You Build Audience Trust
Check out my portfolio, or quickly navigate to your most burning question by clicking the menu below.
Got a question I didn’t answer? Feel free to email me at [email protected] .
The Cybersecurity and Tech Topics I’ve Written About
Here are some of the topics I’ve written about as a freelance cybersecurity writer. I often expand my coverage, so feel free to reach out even if your topic isn’t listed here.
=> Cyberattack prevention and detection
=> Cloud identity management
=> Security metrics
=> Cybersecurity awareness training
=> Company-focused content, such as “about” pages, team bios, “hiring” pages
=> Cybersecurity tools and services
I’ve also written about a variety of other technological topics, including:
=> HealthTech (including QMS, safe and smart water technology, hospital management and more)
=> Smart cities
=> Virtual sales and training labs
=> Automated textile technology
=> Digital court reporting
=> Tech careers
=> Overcoming common PC challenges
=> Technical tutorials for bloggers
=> Company “about” pages, team bios, “contact us” pages, etc
=> EdTech: Accessibility for people managing disabilities
=> Diversity and inclusion in tech organizations
Select Samples from My Portfolio as a Freelance Cybersecurity Writer
Check out select writing samples from my cybersecurity portfolio here. Linking what I can here. Feel free to email me at [email protected] to read the rest.
Cybersecurity Case Studies
How Surveillance Footage Helped a School Diffuse a Potential On-Campus Threat – Verkada
Southeast Asian Country Leads Shutdown of Fake Accounts with a New Intelligence Tool – Digital Clues
Cybersecurity Articles for Municipalities and Countries
$600,000 in Ransomware: Don’t Let the Next Municipality Cyberattack Happen to You – odix
How to Create a Digital Municipality & Remain Safe: Lessons from One of the World’s Smartest Cities – odix
How to Detect Fake Accounts in 10 Minutes – Digital Clues
Cybersecurity Articles for SMB and Enterprise Audiences
How Companies Protect Themselves from Cyberattacks: Enterprises vs. SMEs – odix
A Step by Step Guide to Cloud Identity Management – An identity and access management tech company
Top 8 IIoT Monitoring Solutions for 2023: Pros, Cons & Testimonials – A tech company that simplifies IoT connectivity in the cellular space
Top 9 Threat Hunting Tools for 2023 – Security training platform
7 Crucial Security Metrics Every Engineer Must Know – Data loss prevention software
The Five Cornerstones for an Effective Cybersecurity Awareness Training – Security training platform
AWS GuardDuty vs. Inspector: Which is Right for You? – CDR software company
Why are SMEs So Vulnerable to Cyberattacks? – odix
Working Remotely to Avoid COVID-19? Simple Ways to Protect Your Organization from Hacker Viruses, Too – odix
How to Protect Financial Services from Hackers as COVID-19 Changes Consumer Behavior – odix
Odix Detects Excel Security Breach Days Before it Was Officially Identified – odix
6 Steps to Long Term Cybersecurity Hygiene – odix
The Supplements for Microsoft 365 Mail that Actually Improve Inbox Security – odix
How File Sanitizing Prevents Nearly 100% of Malware (Unrecognizable Threats Included) – odix
Cybersecurity Web Copy
And here are some samples from my portfolio as a cybersecurity copywriter:
[CAREERS PAGE] Behind Every Mission, There are People Who Care – A digital forensics company
[HOME PAGE] Keep Your Company Cybersecure and Compliant – Comsec Global
[ABOUT PAGE] Global Cybersecurity Company Helping the Largest Companies in the World Achieve Their Business Goals – Comsec Global
[TEAM BIOS] Meet the Leadership Team that will Keep Your Company Cybersecure and Compliant – Comsec Global (scroll down the page to read)
Cybersecurity PR Announcements
The EU Awards ODI’s Game Changing Cybersecurity Solutions for SMEs – odix
Meet the New ODI: Why We’re Changing Our Brand to odix – odix
On a Personal Level + The Client that Convinced Me to Become a Freelance Cybersecurity Writer (One of the Best Decisions I’ve Made)
Like most people, technology has always been instrumental to my life. I met some of the most meaningful people in my life online, the opportunity to make a living from writing happened online, and turning dreams into reality – my favorite hobby – is a whole lot easier with the kind of access we have to technology today.
I got my first computer when I was three years old, so I don’t remember a life without one. However, I grew up, like many people who are now in their late 30s, believing the stereotypes and thinking that a career in technology wasn’t for me.
The only ones I saw manage technology around me were boys – my brother and cousins.
So when tech and cybersecurity marketers reached out to see if I’d write their content, I said no. For years. I even once collected recommendations for top cybersecurity writers on LinkedIn because I kept getting requests.
Then, one day, one of my favorite clients became the CMO of a cybersecurity tech company – and decided to bring me along.
I said yes because it was her.
I started researching and writing, and enjoyed the topics greatly. The feedback I got was wonderful. She kept booking more content. I dived in, loving the feeling of expanding further outside my comfort zone, as I’ve practiced in so many areas of my life.
Then another client insisted I’d write cybersecurity content for her.
I decided to go for it.
I embraced my freelance cybersecurity writer self, have loved every moment now for years, and have never looked back.
How Much Does it Cost to Work with an Experienced Freelance Cybersecurity Writer?
Expect to pay at least several hundred dollars per content piece.
The best cybersecurity writers can usually give you a general pricing framework, yet will tailor the final price to your exact needs, so there’s the best cost-gain balance.
Pricing, of course, depends on all kinds of elements, such as…
=> What type of content do you need? Articles are priced differently than case studies.
=> What type of investment does your content require? If it’s research intensive or includes interviews, the pricing might be different.
=> How much content do you need? If you become a regular client, there might be discounts or bonuses.
For example, I offer subscriptions that let you save up to 20% of your budget.
Cybersecurity Content Writer vs. Cybersecurity Copywriter: What’s the Difference? Do You Do Both?
I do indeed do both.
The difference is pretty simple:
=> A cybersecurity content writer usually writes more informational, trust building content, like articles, ebooks and case studies.
=> A cybersecurity copywriter usually writes more conversion-focused materials, such as website copy and sales pages.
Often, the terms are used interchangeably. Feel free to contact me about either need.
Cybersecurity Writer vs. Cybersecurity Technical Writer: What’s the Difference? Do You Do Both?
A freelance cybersecurity writer can lean more toward the technological end of the work – say, write very technical tutorials on how to code cybersecurity functions – or more toward the business side. Some do both. The best cybersecurity writer for you specializes in what matters to you most, so good thing you’re asking.
Personally, I thrive on the business end. I find cybersecurity’s impact on business decision making – as well as the people in your organization and customer base – interesting and important.
But even though I’m not a cybersecurity technical writer, I’ve written about technical topics. Therefore, always feel free to ask.
=> Send me a couple of examples of how techie you want the content to be. It can be from your own organization or something you’ve found online, just so I have a clearer understanding of what technical level you’re looking for.
=> I’ll let you know if we’re a good fit, or maybe ask you further questions to verify.
=> My intention is to help you meet your goals, which means I’m not afraid to tell you I’m not a good fit. If that’s the case, happy to try to refer you if I can.
Here’s what I call “my technical writer portfolio,” AKA some of my techier content:
=> What is an API? A Simple Guide to Non-Techies – Cyara
=> SOC 2 Type II Compliant Live Chat Software: What You Need to Know – Comm100
=> [eBook] The QMS Buyer’s Guide for Device Manufacturers – QMS Company (Please contact me to read it)
=> AWS GuardDuty vs. Inspector: Which is Right for You? – Cloud breach prevention software
How Does Your Business Writing Background Help You Serve My Cybersecurity Audience?
You can be a top cybersecurity writer when it comes to the tech part of it – and that’s crucial – but if you’re oblivious to the business side, you miss a big part of what it takes for organizations to adopt higher quality cybersecurity solutions.
Here are some of the business topics I’ve written about since 2012, and how they contribute to your cybersecurity marketing strategy.
=> Business strategy and execution: If you sell to organizations, you need to build a business case to prove your solution’s urgency across a variety of buying committee roles. You need to help your prospects understand the financial, operational and reputational risks for staying vulnerable to breaches, as well as how to measure cybersecurity success and ROI.
=> Employee experience: To build secure organizations, your clients need to invest in creating a safer culture, plus employee training that actually sticks (instead of forgotten the next day). Even if you “only” sell software, the human element is always there.
=> Customer experience: Understanding customers’ challenges can be integrated into your content in non-salesy ways. If they’re afraid there won’t be tech support or that employees won’t collaborate, we can address it. If they’re providing tech or services themselves, we can talk about the meaning of cybersecurity to their own operations and customers’ trust.
=> Marketing: If you’re reading this, you’re likely a marketer, so working with someone who’s researched, written and practiced so many marketing materials and activities might support you. In addition, if you need to educate prospects on the reputational, branding or trust building risks that a breach can cause, I can help you do that… linking back to the business case and strategy you’ll be able to help prospects create.
Can I Read Your Business Writing Portfolio, Too?
As mentioned above, it’s crucial that the person you choose as the top cybersecurity writer for you understands both the complexities of cybersecurity and those happening behind the scenes, on the business end.
Here’s some of the business writing portfolio I’ve built since 2012. Click the title to read writing samples.
=> ESG (environmental, social and corporate governance)
=> GreenTech
Key Aspects to Consider When Choosing Your Freelance Cybersecurity Writer
This will vary depending on your situation, but generally, consider:
The Writer’s Experience
Have they written about your topic or on similar enough topics, that it’ll be easy for them to close the gap? If it’s close enough, do you feel comfortable trying a (paid) pilot project with them?
Professional writers learn new topics all the time – it’s part of the job description – so if everything else works for you, it might be worth giving a writer you like a chance on a pilot project (say, 1-5 content pieces). Paid pilot projects happen even with the most experienced writers, to verify you work well together, so don’t hesitate to ask.
The Testimonials on Their Website and LinkedIn Profile
Are testimonials specific to clients’ situations?
Not everyone has clients that feel comfortable writing, and some prefer concise testimonials, so don’t necessarily look at length. Just make sure some testimonials say more than “this is the best writer ever.” Ideally, look for a writer that has a bit more info in her or his testimonials, so you can get a sense of what it could be like to work with them.
The Writer’s Availability
Some writers are available at a moment’s notice, or say they can submit content within 7 days every single time, no matter the circumstances. As someone who’s never missed a deadline since I launched my business in 2012, I never commit to something like that in advance.
When you first get in touch, I can give you a general estimate depending on what’s happening in my schedule. When you book me, I will give you an exact, realistic deadline, that leaves time for unexpected “life stuff.” Happy to book you as far in advance as you’d like.
The Writer’s Work Style
Do they require a brief or keyword research? How much hand holding do they need?
Over here, I ask questions when I need to, and do require keywords if you want me to optimize your article for SEO, but generally aim to take as much off your hands as possible if that’s what supports you.
Brief wise – I’ve worked with just a title, fully detailed brief and anything in between. Let’s do what works best for you.
What the Editing Process Looks Like
Some give you a few revisions or never address editing. I’m always happy to get feedback, because the whole point is for the content to help you meet your goals. I provide a full month of unlimited editing requests for each content piece.
Questions to Ask Your Freelance Cybersecurity Writer
Even if you hear that someone is the best cybersecurity writer ever, it’s important to communicate with them (maybe get together on Zoom) before you start collaborating. You’ll be able to ask questions, see their personality, and get a sense of how well you might work together.
Some of the questions you could ask include:
=> What topics have you written about?
=> Can I read some writing samples?
=> Would you be open to doing a (paid) pilot project?
=> What’s your current availability?
=> What’s your usual turnaround time?
=> What do you need from me before you start writing (brief, keywords, intros to management team members you’ll be interviewing, etc)?
=> How open are you to feedback?
=> How many changes can I ask for, and for how long?
Questions Your Freelance Cybersecurity Writer Will Ask You (It’s OK if You Don’t Know All the Answers)
Experienced cybersecurity writers will want to ask you questions, too. For example:
=> Tell me about your company and audience (I want a general idea from you after I’ve read your website in preparation for the initial meeting. Some things come up on intro calls that don’t come up on the website. Then, once we’re officially working together, we’ll do an hour long call to dive deeper into your audience and needs).
=> How technical or business oriented do you need the content to be? (Scroll up for the difference between a cybersecurity technical writer and a business-focused one, although some do both).
=> What type of content do you need?
=> Are you looking for a one time project to fill a gap or for an ongoing collaboration?
=> How often do you need content submitted?
It’s OK if you don’t know all the answers. Don’t let it stop you from contacting a writer or moving forward with your marketing strategy. The idea is to get to know each other and get a sense of whether you’ll be a good fit. You can always try it out with a paid pilot project, and scale it from there.
Ready to Build Trust with Business Leaders? It’s Time for an Experienced Cybersecurity Writer
Contact me today at [email protected], and I’ll help you communicate your value to investors, strategic partners and the customers whose companies you know you can protect.
